The uploader spent his her valuable time to.
Mobile security threats ppt.
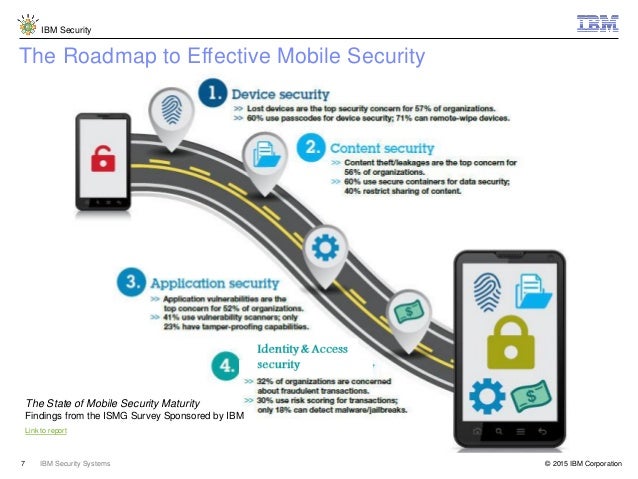
But the bottom line is that it s no longer about the device.
Spyware is a type of malware that infiltrates your device to damage your computer or to gain access to your sensitive information often without your knowledge.
2015 check point software technologies ltd.
Mobile security threats that can affect both android and apple devices spyware.
These threats can disrupt the operation of the smartphone and transmit or modify user data.
One of the most dangerous examples of stealth.
Even within the mobile ecosystem hbr reported that security spending was chronically underfunded relative to mobile app development.
In just the last two quarters of 2012 the number of unique mobile threats grew by 261 according to abi research.
Powerpoint is the world s most popular presentation software which can let you create professional mobile threats attacks powerpoint presentation easily and in no time.
Smartphones popularity and relatively lax security have made them attractive targets for attackers.
This helps you give your presentation on mobile threats attacks in a conference a school lecture a business proposal in a webinar and business and professional representations.
Spyware gathers your personal information and relays it to advertisers data firms or external users.
Advanced persistent threats apts.
Slideshare uses cookies to improve functionality and performance and to provide you with relevant advertising.
According to a report.
John maddison mobile security.
Tis the season for mobile threats.
Applying a zero trust model to mobile and the right security controls at the app level could align productivity and security.
What s next in mobile security threats.
Mobile threats are increasing smartphones or mobile phones with advanced capabilities like those of personal computers pcs are appearing in more people s pockets purses and briefcases.
It s about the applications.
Apts target individuals businesses governments and their data and redirect it via mobile connections.
A smartphone user is exposed to various threats when they use their phone.
Threats in mobile and it s security.
Challenges of smartphone mobile security threats.
If you continue browsing the site you agree to the use of cookies on this website.